Parsec Enabled TLS Demo on Safety Island Communication/HIPC - Baremetal Stock Image
The Parsec-enabled TLS Demo demonstrates secure TLS communication, with cryptographic tasks distributed between user-space software (the TLS client, Mbed TLS libraries) and the secure capabilities (RSE Crypto Service) exposed by the Safety Island Communication/HIPC Baremetal stock firmware image. For more details on the Parsec-enabled TLS demo, refer to the Arm documentation.
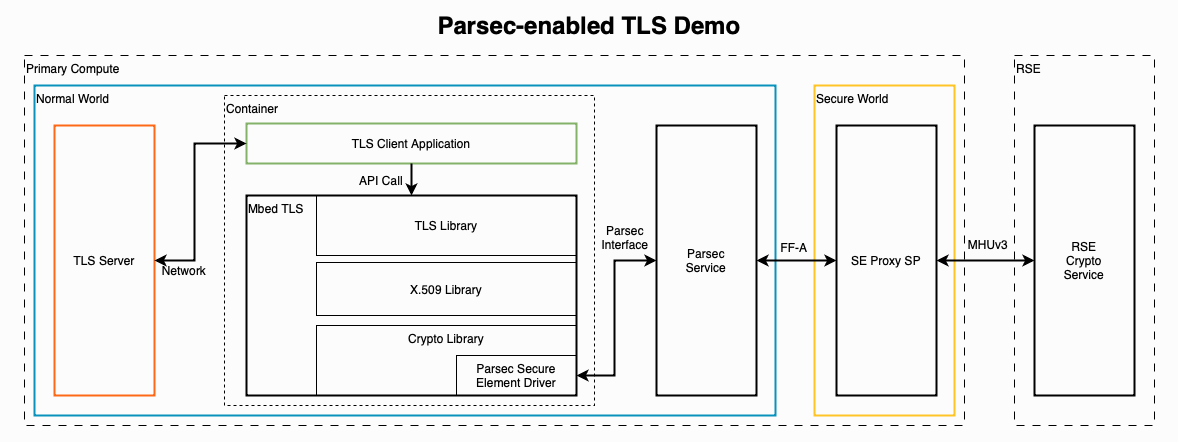
Run the Parsec Enabled TLS Demo
Based on Arm's documentation here.
-
Create a virtual RD-1AE board running the
Safety Island Communication/HIPC (Baremetal) (1.1.1)firmware image. For further details, please refer to the RD-1AE Quickstart guide. -
When the device boots, navigate to the Console tab and select
Primary Compute Non-Securefrom the console selector dropdown. -
Log in as root.
fvp-rd-kronos login: root
root@fvp-rd-kronos:~# -
Check if all the expected services have been initialized:
root@fvp-rd-kronos:~# systemctl is-system-running --wait
running -
Start the
ssl_serverfrom the Primary Compute terminal in the background, you should see a similar output:root@fvp-rd-kronos:~# ssl_server &
[1] 483
root@fvp-rd-kronos:~# . Seeding the random number generator... ok
. Loading the server cert. and key... ok
. Bind on https://localhost:4433/ ... ok
. Setting up the SSL data.... ok
. Waiting for a remote connection ...The TLS client application can take an optional parameter as the TLS server IP address. The default value of the parameter is localhost.
-
Run
ssl_client1from the Primary Compute terminal in a container:root@fvp-rd-kronos:~# docker run --rm -v /run/parsec/parsec.sock:/run/parsec/parsec.sock -v /usr/bin/ssl_client1:/usr/bin/ssl_client1 --network host docker.io/library/ubuntu:22.04 ssl_client1
Trying to pull docker.io/library/ubuntu:22.04...
Getting image source signatures
Copying blob a186900671ab done |
Copying config 981912c48e done |
Writing manifest to image destination
. Seeding the random number generator... ok
. Loading the CA root certificate ... ok (0 skipped)
. Connecting to tcp/localhost/4433... ok
. Setting up the SSL/TLS structure... ok
. Performing the SSL/TLS handshake... ok
. Performing the SSL/TLS handshake... ok
< Read from client: 18 bytes read
GET / HTTP/1.0
> Write to client: 156 bytes written
HTTP/1.0 200 OK
Content-Type: text/h tml
<h2>Mbed TLS Test Server</h2>
ok
. Verifying peer X.509 certificate... ok
> Write to server: 18 bytes written
GET / HTTP/1.0
< Read from server:<p>Successful connection using: TLS-ECDHE-RSA-WITH-CHACHA20-POLY1305-SHA256</p>
. Closing the connection... ok
. Waiting for a remote connection ... 156 bytes read
HTTP/1.0 200 OK
Content-Type: text/html
<h2>Mbed TLS Test Server</h2>
<p>Successful connection using: TLS-ECDHE-RSA-WITH-CHACHA20-POLY1305-SHA256</p> -
Stop the TLS server and synchronize the container image to the persistent storage:
root@fvp-rd-kronos:~# pkill ssl_server
[1]+ Terminated ssl_server
root@fvp-rd-kronos:~# sync -
Perform a software-initated shutdown:
root@fvp-rd-kronos:~# shutdown now